What to Do If You Become a Victim of Cyber Extortion
These days, no one is protected from cyber extortion incidents. And it’s not just big corporations that hackers are going for. They are targeting small businesses, freelancers, and pretty much anyone who uses the Internet.
The numbers are pretty unsettling, too. According to the FBI’s Internet Crime Complaint Center, in the USA alone, the number of cybercrime complaints totaled nearly 860,000, making cybercrime the second most common crime in 2024-2025.
Cyberattacks happen every day, and no one is protected from them. But what do you do if you fall victim to a cybercrime? Here’s a detailed guide on how to handle it if you become a victim of cyber fraud or attack.
1. Don’t Panic
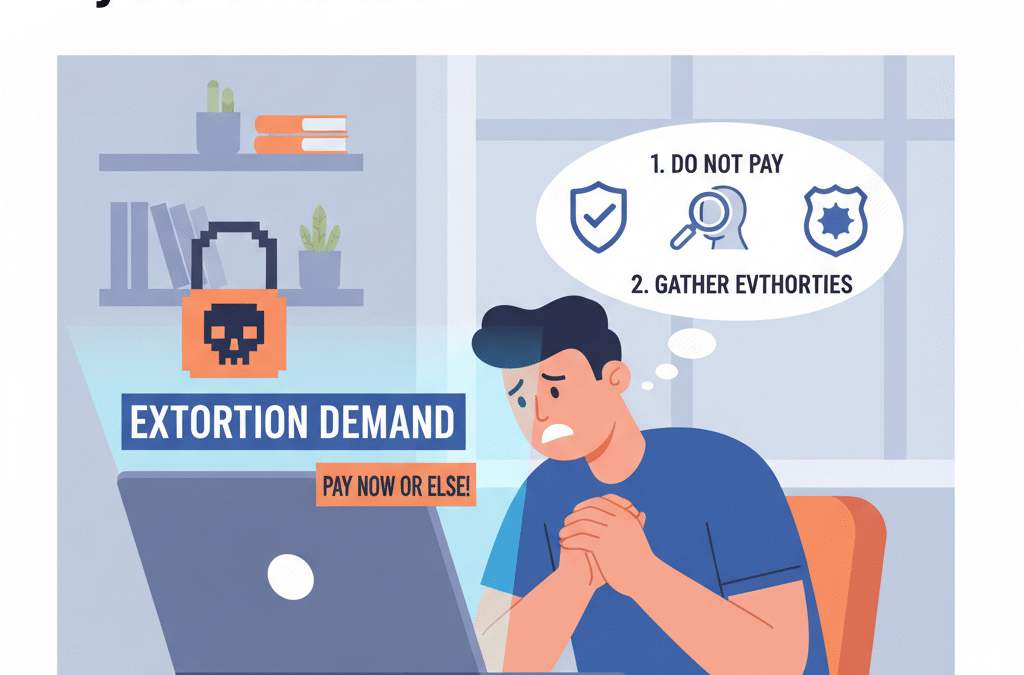
Receiving a message that demands money is discerning. Most people get scared and make rash decisions they later regret. But don’t take that bait. If you agree to pay any money, things can get even worse.
Unfortunately, paying doesn’t guarantee anything. Hackers won’t necessarily give your files back or stop threatening you. In fact, most often they won’t. Once the criminals know you’re willing to pay, they will come back to ask for more.
In this situation, it’s important to stay calm and keep a cool head. Instead of panicking, start collecting evidence. You need screenshots of every threatening message or email you receive. This will serve as proof when you turn to the authorities or a security expert to report fraud.
2. Disconnect and Contain the Threat
Now, you need to stop the attack from spreading. Here are a few steps to do it right:
- Unplug your device from the Internet, including Wi-Fi and Bluetooth.
- If it’s your work network that’s been affected, let your IT team know right away.
- Turn off any automatic syncing so malware doesn’t reach your cloud backups or shared folders.
- Don’t plug in a USB or any external drive until you’re 100% sure the malware’s gone.
These simple steps will help you limit hacker access to your systems and protect your other devices from being hacked.
3. Report the Incident
Cyber extortion is a crime—no less serious than theft. Start gathering your evidence: screenshots, ransom notes, emails, anything that shows what happened. Then, reach out to your local law enforcement. In the U.S., for example, you can file a complaint with the FBI’s Internet Crime Complaint Center. Other countries have similar cybercrime agencies.
When you report it, provide as many details as you can:
- When and how the attack started;
- What data or systems were affected;
- Any demands or threats from the hackers;
- Evidence of payment requests or how they contacted you.
Even if the hacker’s not local, it’s still worth reporting. Cyber police can sometimes connect your case with others that follow the same pattern.
4. Contact Your IT or Cybersecurity Provider
If you work for a company, it’s time to involve your cybersecurity team. They will assess the full extent of the damage and remove any malware or scripts running in the background.
If you don’t have your own team, you can hire a crisis management firm. They will help you recover lost data and install robust defense tools to prevent future cyberattacks.
The best option is to have cyber extortion coverage. In cases like these, it proves invaluable. Most policies cover not only technical investigations and data recovery but also legal or PR support in the event of damage to your reputation. Without it, dealing with the consequences of cyberextortion can result in significant out-of-pocket expenses.
5. Inform Affected Parties
If hackers stole customer data or employee records, you have to let those people know. It might feel embarrassing, but honesty is crucial. Besides, most countries have strict laws about reporting data breaches, and any attempt to disclose a breach can lead to fines or even lawsuits.
6. Take Security Measures
Once the threat has been found and removed, you need to act quickly. The fact that your system was affected means it’s got weak posts that need fixing.
These simple steps can help prevent future attacks:
- Update your passwords;
- Enable two-factor authentication on all accounts (if you’ve not done it before);
- Patch your software or operating systems immediately.
Additionally, consider getting a subscription for cyber extortion protection tools or services. These may include firewalls and anti-malware, while others may also include insurance coverage for any financial losses involved. The goal is to safeguard your system and make it invulnerable to hackers.
7. Back Up and Recover Your Data Safely
If your files have been encrypted or locked, the best and safest way to recover them is to restore them from backups. That’s why it’s crucial to regularly create off-site backups.
After completely removing malware, use your clean backups to restore your systems. Never restore data until your devices have been fully scanned and cleared; otherwise, you risk reinfection.
If you didn’t have backups this time, don’t worry. Create a reliable backup plan, including cloud-based copies, to avoid losing data if your systems get ever hit again.
Final Thoughts
Cyber extortion is one of those things you hope never happens. But it does happen, and it happens more often than you’d think. That’s why cybercrime awareness is vital, and investing in the right tools from the start makes all the difference.
While no one is immune to an attack, those who have cyber extortion coverage are usually in a better position to recover quickly and minimize the damage. This kind of insurance not only helps recover financial losses but also connects you with cybersecurity professionals who can deal with any consequences of an attack, including lawsuits.
Even if you don’t have one, remain calm and act quickly. By reporting the incident to the authorities and taking security measures, you can stop the damage from spreading and protect your sensitive data.























